If you are confused between truststore and keystore and looking to find what exactly they mean then you have come to the right place. Earlier, I have shared free Java courses and today, I am going to tell you the difference between trustStore and keyStore in Java. Both trustStore and keyStore are important but confusing concepts and constantly tormented Java developers when they connect to servers using SSL. The main difference between trustStore vs keyStore is that trustStore (as the name suggest) is used to store certificates from trusted Certificate authorities(CA) which are used to verify certificate presented by Server in SSL Connection while keyStore is used to store the private key and own identity certificate which program should present to other parties (Server or client) to verify its identity.
That was a one-liner difference between trustStore vs keyStore in Java but no doubt these two terms are quite confusing not just for anyone who is the first time doing SSL connection in Java but also for many intermediate and senior-level programmers.
One reason for this could be SSL setup being a one-time job and not many programmers get the opportunity to do that.
In this Java article, we will explore both keystore and trust stores and understand the key differences between them. You can also use a keytool command to view certificates from truststore and keystore. keytool command comes with Java installation and it's available in the bin directory of JAVA_HOME.
In this Java article, we will explore both keystore and trust stores and understand the key differences between them. You can also use a keytool command to view certificates from truststore and keystore. keytool command comes with Java installation and it's available in the bin directory of JAVA_HOME.
By the way, if you are new to the Java world and want to learn more about basic and advanced Java concepts in a structured way then there is no better way than to join an online course like The Complete Java Masterclass by Tim Buchalaka on Udemy. This 80+ hour course is the most up-to-date and comprehensive course to learn Java.
Difference between KeyStore vs TrustStore in Java
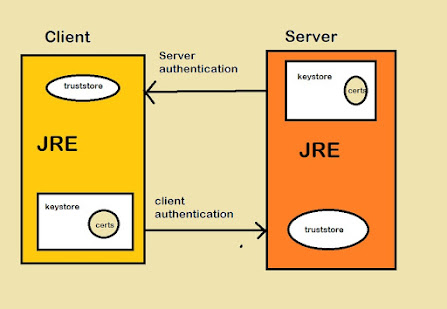
In order to understand the difference between keyStore and trustStore you need to understand How SSL conversation happens between client and server because this is the starting point of confusion, many Java programmer doesn't pay attention whether they are implementing the server side of SSL connection or client-side of SSL Connection.
One example is setting up SSL for tomcat on is server-side of SSL while setting up JDBC over SSL is the client-side of SSL connection. If you are implementing SSL on Server side you need a KeyStore to store your server certificate and private key.
Anytime a client will connect to the server, the server will present its certificate stored in KeyStore and the client will verify that certificate by comparing it with certificates stored on its trustStore.
One example is setting up SSL for tomcat on is server-side of SSL while setting up JDBC over SSL is the client-side of SSL connection. If you are implementing SSL on Server side you need a KeyStore to store your server certificate and private key.
Anytime a client will connect to the server, the server will present its certificate stored in KeyStore and the client will verify that certificate by comparing it with certificates stored on its trustStore.
If you are interested to learn more about client-server architecture and distributed systems then I highly recommend Distributed Systems & Cloud Computing with Java course by Michael Pogrebinsky on Udemy.
Let's see the difference between truststore vs keystore in point format which is much clear and easy to understand :
1. Keystore is used to store your credential (server or client) while truststore is used to store others' credentials (Certificates from CA).
2. Keystore is needed when you are setting up server-side on SSL, it is used to store server's identity certificate, which server will present to a client on the connection while trust store setup on client-side must contain to make the connection work. If your browser connects to any website over SSL it verifies the certificate presented by the server against its truststore.
3. Though I omitted this in the last section to reduce confusion you can have both keystore and truststore on the client and server-side if the client also needs to authenticate itself on the server. In this case, the client will store its private key and identify the certificate on the keystore and the server will authenticate the client against the certificate stored on the server's trust store.
4. In Java -javax.net.ssl.keyStore property is used to specify keystore while -javax.net.ssl.trustStore is used to specify trustStore.
5. In Java, one file can represent both keystore vs truststore but it's better to separate private and public credentials both for security and maintenance reasons.
6. When you install JDK or JRE on your machine, Java comes with its own truststore (collection of a certificate from well known CA like Verisign, GoDaddy, Thawte, etc. you can find this file inside
JAVA_HOME/JRE/Security/cacerts where JAVA_HOME is your JDK Installation directory.
7. keytool command (binary comes with JDK installation inside JAVA_HOME/bin) can be used to create and view both keyStore and trustStore.
That's all about the difference between truststore and keystore in Java. If you are still not clear with what is truststore and keystore in Java or the difference between keystore and truststore then just remember one line keystore is used to store the server's own certificate while truststore is used to store the certificate of other parties issued by CA like Verisign or GoDaddy or even self-signed certificates.
Other Java Programming Articles you may like
- The Complete Java Developer RoadMap (roadmap)
- 5 Courses to Learn Java Multithreading in-depth (courses)
- 10 Java Multithreading and Concurrency Best Practices (article)
- 5 Essential Skills to Crack Java Interviews (skills)
- How does Exchanger works in Java Multithreading (tutorial)
- Top 50 Multithreading and Concurrency Questions in Java (questions)
- 10 Courses to learn Java for Beginners (courses)
- Difference between CyclicBarrier and CountDownLatch in Java? (answer)
- How to avoid deadlock in Java? (answer)
- Understanding the flow of data and code in Java program (answer)
- How to do inter-thread communication in Java using wait-notify? (answer)
- 10 Tips to become a better Java Developer (tips)
- Top 5 Books to Master Concurrency in Java (books)
Hi
ReplyDeleteStill Im confused with point-3
That is we can configure both keystore and truststore in tomcat .
Means , is it like configuring the truststore in server.xml is equivalent to configuring the system property java.net.ssl.truststore or is it different
And also , Can u suggest test scenario on how to verify whether it is working fine after configuring
To explain it better. Truststore basically contains the certificates of CA which actually contains the public key(RSA) of CAs.
ReplyDeleteOne publishes its public key but not private key. Trust Store contains public keys of well known CAs. These public keys are used to verify if the server you are trying to connect is legitimate.
Keystore and truststore are actually same. To be precise Truststore is a keystore. Keystore is a more generic term. No one stops you from storing a private key in a Truststore. The name Truststore is given to a keystore which only contain public keys. So the name Truststore is because of the content.
Ref:http://download.java.net/jdk8/docs/technotes/guides/security/jsse/JSSERefGuide.html#ConfigSmartcard
Can anybody explain the each line of how these keystore/truststore works in SSL OR some reference?
ReplyDeleteAs you said, "keystore is used to store server's own certificate while truststore is used to store the certificate of other parties issued by CA"
ReplyDeleteNow, server has its own keystore.when client comes to server having any other truststore then as they will have different keys they will never authenticate themselves.
How can they authenticate for correct key when server has own key and client has trustore from CA ?
The Server's certificate (signed by a CA's private key) is presented to the Client during the SSL handshake. The client browser validates this certificate by using the corresponding CA's public key stored in the client's trustStore. Since the CA's public and private key are matched pairs, a successful decryption indicates to the browser/client that the certificate issuer (CA) has indeed issued this certificate to the server. This allows the client to 'trust' the server's identity.
DeleteBoth keystore and truststore are files. Password protected files. The stuff that you can store into this file are key/value pairs. For example, a key (or otherwise known as the alias) of "color", and a value of "green". Such that, later on, you query into this file by specifying the key (or alias) and it gives you its associated value. Whereas the key is a string, the value comes in a few standard known formats. The value could be a certificate, or it could be a private key. But because both files are of same format, you can also store a certificate in a keystore. You can store a private key in a truststore. You can store a jpeg image into a keystore or truststore. You can store an mp3 etc.
ReplyDeleteThat's nice explanation, thanks for adding value through your comment.
DeleteThe two very different uses of "key" here may be a source of confusion for some.
DeleteThe "key" or "name" or "alias" part of a "key,value" pair is just like a variable name, and the "value" part is, well , its value. But in the context of ssl, the useful elements of a keystore or truststore have "keys" which are basically the names of cryptographic keys and those cryptographic keys are the main part of the content of the corresponding values. And although keystore and truststore have the same format, they are distinguished by the different occasions on which we want to read from them. Would putting public keys from all the trusted CAs (along with perhaps your mp3 collection) in the same file as a server's keystore have any performance cost due to looking in a very big file to find the certificate that it wants to pull and deliver on every new connection?
Thank Alan for making it clear.
DeleteThis one is also failed to describe keystore vs truststore. That jdbc-SSL analogy is great but then I got lost when He explain what keystore is . Did he refer to server or client keystore?
ReplyDeleteHello Anonymous, what is your doubt? there is nothing like server or client, its very simple truststore and keystore are just a text file containing certificates.
DeleteDoes truststore and keystore are only in jks format or there is any other format that is used ??
ReplyDeleteHello Vivek, as much I know its jks format so that keytool utility can read and write it. Is there any scenario where you need in different format?
DeleteI have keystore as pkc12 format and truststore as jks format . Will this conflict ?
ReplyDeletevery good article.. Indeed very useful from basic point of view. Perhaps if you can create/share any article for making a java http client for connecting to rest server via SSL certificate and token both.
ReplyDelete